
Data is the lifeblood of any organization. With workers now accessing data from a range of devices and locations—from Federal agencies to Starbucks—the traditional perimeter has been rendered obsolete and the risk of data breaches has grown. As federal agencies adapt to this new threat landscape, they need to secure access for their now-distributed workforce and provide data protection. That can’t be done without a data-first approach to Zero Trust architecture.
The Department of Defense breaks Zero Trust into seven pillars, each of which is a key focus area for implementation of Zero Trust controls. The first five pillars are users, devices, networks, applications, and data. As seen below, the last two pillars build on the first five.
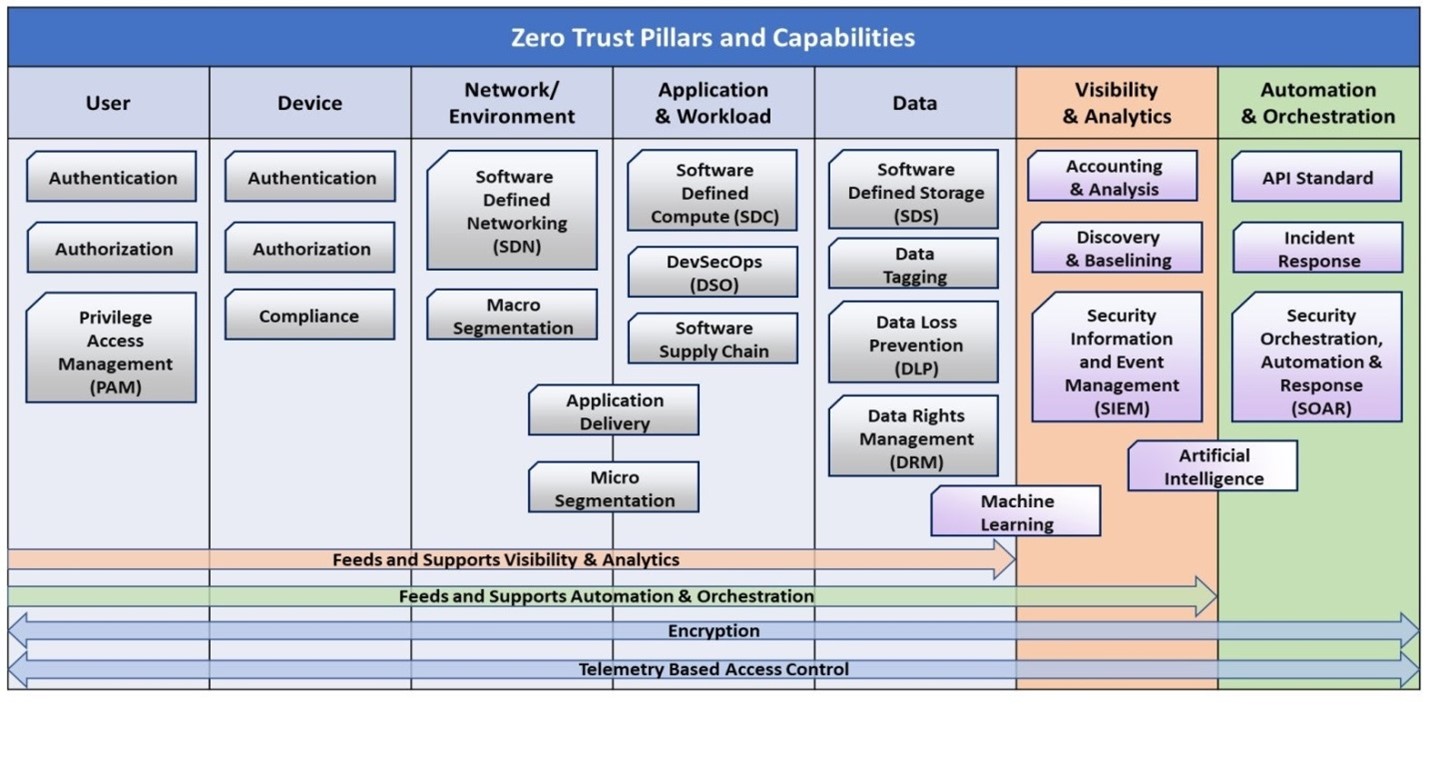
With regard to data, federal agencies must have a comprehensive data management strategy (i.e. encrypting data at rest and in transit) as well as data loss prevention (monitoring, analysis, and control of data whether in use, in transit, or at rest) strategies in place. Data Loss Prevention (DLP) tools are endpoint protection systems that watch what a user does when they interact with data. But as the existence of other pillars suggests, a true Zero Trust approach doesn’t stop there.
The DoD’s sixth pillar is analytics: breaking down silos between the first five pillars to have a holistic or unified understanding of data, applications, networks, users, and devices. A data-first approach to Zero Trust integrates DLP into the broader architecture with an eye towards the continuous evaluation of threats—and the ability to automatically and quickly respond to them.
Put another way, agencies must be able to contextualize the use of data (how users interact with data and what data they’re accessing) for any given user over the entirety of the Zero Trust framework, including how the user interacts with devices, networks, and apps. Even when access is granted to a particular user, Zero Trust means continuing to monitor that access for red flags. By integrating DLP into a broader Zero Trust architecture, agencies can engage in forensic analysis, confidence scoring, and policy automation.
If an authorized user starts to access sensitive data they normally don’t interact with or starts doing so at odd hours or from a suspicious location, that anomalous behavior—likely an indicator of a data breach—will be flagged. The seventh and final pillar is automation and orchestration: dynamically modifying that user’s access privileges to stop the breach in real-time. Sometimes, that may mean requiring additional authentication steps. Other times, further access to data may be barred altogether.
In its early stages, Zero Trust focused heavily on identity and access. Now, organizations are increasingly realizing that data protection is paramount. Many agencies are turning to Secure Access Service Edge (SASE) to handle access to applications, networks, and devices—what’s coming in and out—through a converged cloud service. But agencies must also know what’s going on inside the network: who’s looking at data and how. That means not just implementing DLP and related tools but integrating them with the other focus areas.
Protecting data is top of mind for federal agencies, and for good reason. By taking a data-first approach to Zero Trust architecture, agencies can continuously vet and monitor users and data, keeping users safe wherever and however they log in. This enables agencies to deploy dynamic data policies, as opposed to relying on the outdated traditional perimeter and its all-or-nothing approach.
Zero Trust has five major tenets:
- Assume a Hostile Environment. There are malicious personas both inside and outside the network. All users, devices, and networks/environments are treated as untrusted.
- Presume Breach. There are hundreds of thousands of attempted cybersecurity attacks against DOD networks every day. Consciously operate and defend resources with the assumption that an adversary has the presence within your environment. Enhance scrutiny of access and authorization decisions to improve response outcomes.
- Never Trust, Always Verify. Deny access by default. Every device, user, application/workload, and data flow are authenticated and explicitly authorized using least privilege, multiple attributes, and dynamic cybersecurity policies.
- Scrutinize Explicitly. All resources are consistently accessed in a secure manner using multiple attributes (dynamic and static) to derive confidence levels for contextual access to resources. Access to resources is conditional and access can dynamically change based on action and confidence levels resulting from those actions.
- Apply Unified Analytics. Apply unified analytics for Data, Applications, Assets, Services (DAAS) to include behavioristics, and log each transaction Zero Trust assumes continued and mandated use of communication encryption to the greatest extent possible. The use of mutual authentication of users with client certificates to web applications has long been the effective standard. The DOD is making strides to improve access to data by approving multiple authenticators and authorization schemes to better improve usability and access while maintaining security and visibility.
Zero Trust - Executive Order
Last year there was a 10-fold increase in the severity of data breaches, so it’s not surprising that the Biden administration’s recent Executive Order on Improving the Nation’s Cybersecurity called for federal agencies to adopt a Zero Trust approach in an effort to prevent further damage.
According to the EO, federal government agencies must develop plans to adopt Zero Trust architectures within 60 days following the issuance of the order. The EO also requires agencies to implement a series of migration steps, create a schedule for implementation, identify activities that will have the most immediate security impacts, and more.
But what is “Zero Trust”? How is it defined? What are its key components?
Confusion around Zero Trust
The EO doesn’t really go into a great amount of detail regarding the components that should be included in Zero Trust architecture. It does specifically say that agencies should “incorporate, as appropriate, migration steps that the National Institute of Standards and Technology (NIST) outlined in standards and guidance.” That is a good start and provides a framework upon which agencies can and should build.
That is important because to this point there has been no standardized definition of Zero Trust architecture. Indeed, although many government agencies have already begun to adopt their own versions of Zero Trust, there has been very little consistency amongst different models. For example, earlier this year the Pentagon introduced zero-trust architecture for the Department of Defense that includes complex capabilities taxonomy tailored specifically to the DoD’s unique requirements. Meanwhile, other agencies, including NIST, the Air Force, the General Services Administration (GSA), and others have their own Zero Trust models.
The Department of Defense’s Zero Trust architecture (Source: Department of Defense Zero Trust Reference Architecture)
A survey from several Institutions shows the various approaches that organizations are using to create their own Zero Trust architectures. According to respondents, 47% are basing their approach on NIST 800-207; 39% on the Forrester Zero Trust Model; 32% on Gartner’s Continuous Adaptive Risk and Trust Assessment (CARTA); and 25% on Gartner’s Secure Access Service Edge (SASE). The rest have created their own. The results are a testament to the lack of uniformity when it comes to building a Zero Trust environment.
Consistency and standardization simplify complex challenges, and cybersecurity is one of the most complex challenges facing government today. Having too many variations only adds greater complexity and confusion, both of which inhibit agencies’ abilities to successfully implement Zero Trust.
Zero Trust architecture requires a balanced approach to security
In the absence of Zero Trust standards, agencies should ensure they take a balanced approach when adopting Zero Trust architecture. Ultimately the end goal is not about compliance, but about the results of the pieces of the architecture coming together. Many technologies can offer important pieces toward Zero Trust, but ultimately inter-dependency of behaviors across users, devices, applications, and data matter.
Zero Trust architecture integration - Policies with the user and device ID, ZTNA and DLP
Zero Trust is not just a means of controlling who is able to access a government network, but there’s much more to Zero Trust than just user and device identification. For example, the methodology has evolved to also include Zero Trust Network Access (ZTNA), which provides better attack surface management by encrypting applications and segregating them from the wider Internet.
Over-rotating toward a single technology as part of Zero Trust architecture leaves holes in your security architecture. NIST 800-207 recognizes this and as one of the tenets for Zero Trust suggests “Access to resources is determined by dynamic policy—including the observable state of client identity, application, and the requesting asset—and may include other behavioral attributes…Behavioral attributes include automated user analytics, device analytics, and measured deviations from observed usage patterns.”
Zero Trust - data loss prevention with behavioral attributes for continuous adaptive Zero Trust
With Zero Trust there’s still the problem of data visibility. A single user could be downloading one file or billions. Unfortunately, since DLP (Data Loss Prevention) is often siloed off from the rest of a Zero Trust architecture, administrators may know who’s accessing their applications or network, but they do not have a clear picture of who is downloading what or how much. Without integrating DLP into the rest of the architecture, administrators can’t accurately determine whether or not their data is secure.
An effective Zero Trust architecture drives agencies towards a more data and user-centric approach while moving away from being perimeter-centric. Integrating DLP with behavioral analytics enables your Zero Trust architecture to have:
- Individualized adaptive data policies
- Behavioral analytics-driven insights
- Data discovery and classification
- Maximizing security analyst efficiency and reducing fatigue
Using behavior-based cybersecurity, your security adapts to changing levels of risk. This includes enterprise-wide visibility (network, endpoints, and cloud). This enables detection when people are exhibiting risky behavior: their risk score changes depending on how they behave at any time, allowing security to tighten targeted policies and block actions if required. This helps security teams decide what is innocent or suspicious based on behavior in context, reducing false positives by leveraging intelligent data security to revisit decisions as you and your machines learn.
An effectively implemented Zero Trust architecture incorporates user identification and behavioral analysis, attack surface mitigation, and data management for continuous and adaptive Zero Trust. Together, these components are important to helping agencies achieve the Executive Order’s goal to “identify, deter, protect, and respond” to cyber threats.
Zero Trust - are you really practicing security?
The recent Log4J vulnerability opens up a scary question about web security approaches, if you aren’t using a Zero Trust approach then are you really practicing security?
From a security and risk mitigation perspective you want an approach that is consistently effective, especially when a newly discovered vulnerability is being actively exploited. However, the Log4J vulnerability renders virtually every website potentially compromised. This means that web security solutions that only rely on reverse DNS resolution or IP reputation are ineffective – websites cannot be currently trusted to be safe. Web gateways provide a better level of protection by actively scanning web content for malware, but this still relies on the effectiveness of detection and response to work and eventually a zero-day can find its way through the defenses.
The only high assurance web security, the only web security that provides a Zero Trust approach is Remote Browser Isolation (RBI). RBI technology treats all websites as compromised from the outset and provides a safe way to view and interact with webpages, regardless of what malware is present. RBI does this by separating the active browser session from the user’s desktop, and streaming video of the interaction back to the user. Any malware is simply left behind in the remote, isolation container, and that virtual container is deleted at the end of the browsing session along with any malware that was encountered.

