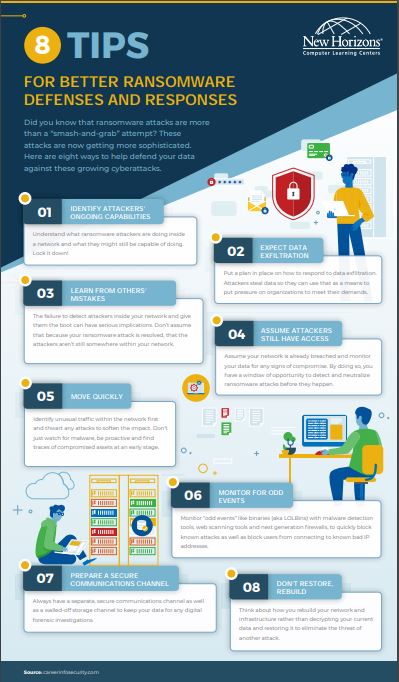
Did you know that ransomware attacks are more than a “smash-and-grab” attempt? These attacks are now getting more sophisticated.
Here are eight ways to help defend your data against these growing cyberattacks.
- IDENTIFY ATTACKERS’ ONGOING CAPABILITIES
- EXPECT DATA EXFILTRATION
- LEARN FROM OTHERS’ MISTAKES
- ASSUME ATTACKERS STILL HAVE ACCESS
- MOVE QUICKLY
- MONITOR FOR ODD EVENTS
- PREPARE A SECURE COMMUNICATIONS CHANNEL
- DON’T RESTORE, REBUILD